Open the M365 admin center, and click on "Users", "Active users."
Click the "User templates" button.
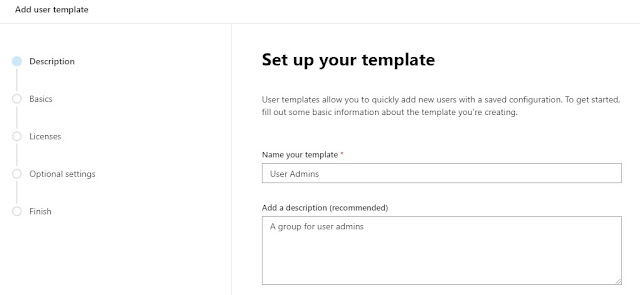
You will get this window. Enter your template details i.e. give it a name and a good description.
Click "next". Select your location and license on the next screen. Be aware that the license you choose here will be applied to any new user made from this template.
I have selected no license here because it is a template for my User admin accounts. I have also left the location as United States because that is where my test tenant is based.
Click "next", check the options and click the "Finished adding" button.
You may also get the black box you can see in the bottom right of the screen above which asks if you will talk to Microsoft about your experience. This is because it is a new feature and they like to get feedback from early adopters. I clicked on this, only for them to say there was no active session. Nobody wanted to speak to me, sob, sob.
From here, you can click "Add a user using this template". I have clicked "Finish" and come out of it to show how a user can be created from the M365 admin center.
Click "User templates" and select your template.
Fill out the names, username and display name. The rest is done for you. You can scroll down to check the options but you cannot change any other fields.
Click add and you are done. Simples!
Click the "User templates" button.
You will get this window. Enter your template details i.e. give it a name and a good description.

Click "next". Select your location and license on the next screen. Be aware that the license you choose here will be applied to any new user made from this template.
I have selected no license here because it is a template for my User admin accounts. I have also left the location as United States because that is where my test tenant is based.
You may also get the black box you can see in the bottom right of the screen above which asks if you will talk to Microsoft about your experience. This is because it is a new feature and they like to get feedback from early adopters. I clicked on this, only for them to say there was no active session. Nobody wanted to speak to me, sob, sob.
From here, you can click "Add a user using this template". I have clicked "Finish" and come out of it to show how a user can be created from the M365 admin center.
Click "User templates" and select your template.
Fill out the names, username and display name. The rest is done for you. You can scroll down to check the options but you cannot change any other fields.
Click add and you are done. Simples!






Comments
Post a Comment